Security Features for eCommerce Website

“After a cyberattack, the company suffered massive losses…” Headlines like this are all too common, and it’s no surprise. Data security remains one of the most critical challenges businesses face today.
At Expert Soft, we’ve faced these challenges head-on in our enterprise projects, ensuring our clients’ websites remain secure. We’ve created this guide to share insights into how to secure ecommerce websites. While it doesn’t promise a cure for every risk, it offers valuable knowledge to help you better understand and defend against potential ecommerce security threats.
As technology advances, security measures evolve, however, attack methods are evolving even faster. This constant battle leads to serious reputational and financial damage for companies. According to McKinsey, cyberattack damage is projected to reach $10.5 trillion annually by 2025.
For large ecommerce platforms, the stakes couldn’t be higher. With millions of transactions, vast customer databases, and countless third-party integrations, the vulnerabilities multiply. That’s why ecommerce website development services shouldn’t just fix existing weaknesses, they should focus on proactively safeguarding the entire system from future threats.
What Are the Common Ecommerce Security Attacks?
As users entrust ecommerce websites with their personal data and security company web measures aren’t always strong enough, the ecommerce industry has become as attractive to cybercriminals as the financial, healthcare, and manufacturing.
Attacks can target employees and end-users, exploit technical vulnerabilities or human error. While the methods may vary, many attacks share common features, which help categorize them.
So, to establish robust security for ecommerce sites, you should implement security practices that address the following ecommerce security threats.

SQL injections
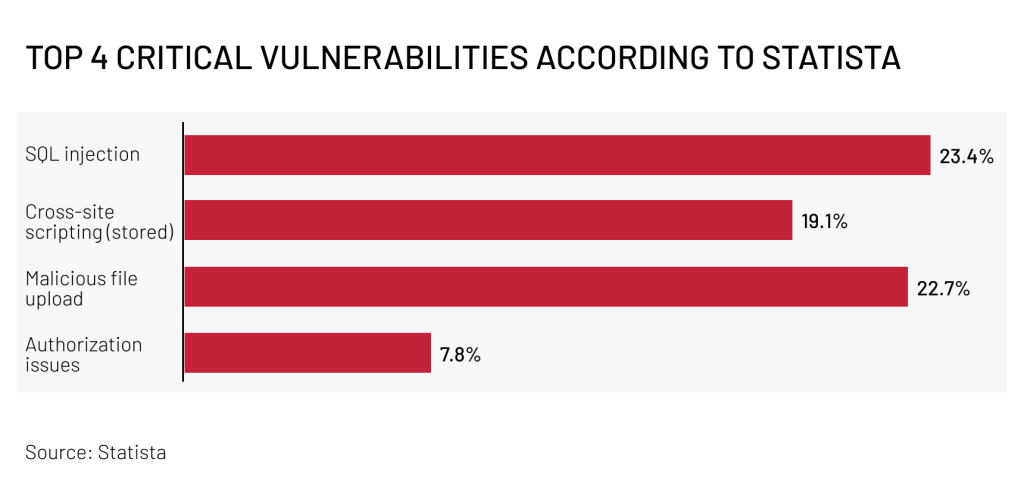
SQL injection attacks are as old as the web itself, but don’t let their age fool you — they rank first among critical vulnerabilities for compromising the security of an online store according to Statista.
At its core, SQL injections allow bad actors to manipulate the queries your website sends to the database by injecting malicious SQL code into input fields, such as login forms, search bars, or any data entry points connected to your database.
In this way, attackers can extract sensitive information. While passwords are typically hashed, making them difficult to reverse, attackers can still gain valuable data, such as email addresses, home addresses, etc. In more severe cases, they could even manipulate the database to delete or modify data.
SQL injections hit where it hurts the most: customer trust and data integrity. A successful attack can lead to:
- Financial loss due to fraudulent transactions.
- Regulatory penalties for failing to protect sensitive user information (think GDPR fines).
- Reputational damage when customers discover their personal data has been compromised.
The root of this vulnerability lies in improper handling of user inputs, when data from the user is combined directly with SQL queries without proper validation.
To avoid this, always sanitize input data before it interacts with your database. Also, you can use parameterized queries (prepared statements) that instead of directly injecting user inputs into SQL queries treat them as data rather than executable code. This ensures any input data, no matter how malicious, is handled securely.
The good news for SAP Commerce users. The platform includes built-in protections against SQL injections, automatically sanitizing and validating user inputs before they even reach the database, putting you one step ahead in the ecommerce cybersecurity game.
Cross-site scripting (XSS) attack
With 19.1% of critical vulnerabilities globally attributed to stored XSS, this type of security attack poses a serious threat, especially for an ecommerce platform loaded with user-generated content and dynamic interactions.
Unlike SQL injections that target your database, XSS goes after your users. It often pairs with social engineering to trick unsuspecting visitors into executing harmful scripts.
Here’s how it works: a bad actor might embed a script in a product review, which then gets stored in your database. The next user to explore that review unknowingly triggers the script, which can steal their session cookies or even send a request to the server to change their account details, e.g. a phone number, giving the attacker a way to hijack their account. This is stored XSS online fraud in action.
Another option is reflected XSS, which occurs when an application includes data from an HTTP request directly in its response without proper validation. It’s a one-time reflection of the malicious code.
Keeping XSS at bay requires proper input validation at every step:
-
Sanitize inputs.
Strip out any potentially harmful tags and ensure no JavaScript or executable code can sneak into your database.
-
Use JSP tags for output.
This ensures that even if malicious code makes it into your system, it won’t execute when displayed on the webpage.
Malicious software
While malware doesn’t usually target website users directly, it poses a significant threat to your internal team. The moment an employee unknowingly downloads malicious software, it opens a backdoor to your system. And it’s not just about bad luck — 74% of confirmed breaches are due to human error, according to the 2024 State of Email & Collaboration Security Report by Mimecast.
How can malware get into your system? Here’s a real-world example from one of Expert Soft’s projects with a luxury retail company.
The website’s support page allowed users to attach PDF files when submitting inquiries. Sounds harmless, right? However, attackers could attach a malicious PDF file loaded with a harmful script. Once an unsuspecting employee opens the file, the script could execute.
In this case, the client took a simple approach: they removed the file upload feature altogether because it was rarely used. However, there are some less radical ways for data breach prevention due to malware, such as malware scanning tools with a high detection rate or libraries designed to scan and clean files of malicious scripts and hidden code.
Also, ensure that your team is using the latest versions of operating systems and applications. Many malware attacks exploit vulnerabilities in older versions, and regular updates can strengthen security.
DoS and DDoS attacks
In the first half of 2024 alone, Cloudflare mitigated 8.5 million DDoS attacks according to the Cloudflare DDoS Threat Report. These security attacks, whether from a single source (DoS) or multiple sources (DDoS), flood servers with overwhelming requests, consuming resources and ultimately crashing your website.
For ecommerce platforms, this can be catastrophic, especially during high-traffic events, such as Black Friday sales. At these peak times, your website is already under heavy load, making it even more susceptible to attacks. So, strengthening the security of an online store should be a top priority to ensure uninterrupted service.
There are multiple security measures to defend against this type of attack.
-
Web application firewall (WAF)
WAF filters incoming web traffic, blocking malicious traffic before it hits your servers.
-
Content Delivery Network (CDN)
Expert Soft uses Akamai in some projects to distribute the site's content across several servers and absorb attacks.
-
IP address and session blocking
When detecting a flood from a single IP address, the server should block both the IP and session cookies.
And again SAP Commerce Cloud users are leading the way. The cloud platforms are more resilient to DDoS attacks because of their distributed server architecture, making it harder for attackers to overwhelm the system.
Remote code execution (RCE)
Remote Code Execution (RCE) allows bad actors to execute malicious code directly on your server, essentially taking control of your system from afar.
RCE vulnerabilities occur when attackers exploit weaknesses in your code, often through admin panels or forms that accept inputs. If your site allows any kind of code execution without strict validation and controls, you’re leaving the door open for attackers to run their code.
To avoid this, developers must ensure that no part of the application’s code allows for arbitrary execution of other code. Following the best coding practices and using safe libraries is key here.
While RCE is less common for storefronts, admin panels are prime targets. To secure them, ensure that access to the admin area is protected with a password that complies with password strength requirements. Also, limit access to sensitive areas of the website by requiring users to log in via a corporate VPN. This restricts entry points and keeps out external threats.
Disclosing excessive information in error messages
Error messages are a necessary part of any application, but they can sometimes reveal far more information than intended, both to users and in server logs. Disclosing excessive information, such as credit card numbers, passwords, or other critical data, can accidentally hand attackers the keys to your system.
Protecting your website from this vulnerability requires a proactive approach to error management and secure logging. Here, static code analysis tools, such as Veracode, can help.
For example, when our client, a luxury retail company, was certified for PCI DSS compliance, our team used Micro Focus Fortify to scan the code against a comprehensive set of security rules. One of the certification requirements was ensuring secure logging, but with millions of lines of code in enterprise ecommerce projects, manually detecting vulnerabilities is nearly impossible. The tool efficiently identified issues, enabling our team to resolve them and receive the certification.
9 Security Measures for Ecommerce Websites
The common security practices for ecommerce websites include the following.

Make sure to have an SSL certificate
SSL certificates are not just a security measure for ecommerce websites, they are the foundation of user trust. By enabling encrypted communication between a user’s browser and your website, an SSL certificate ensures that all data, whether it’s personal details, payment information, or login credentials, travels securely.
But encryption strength isn’t the only benefit. An SSL certificate also authenticates your website, proving that it’s genuine and protecting users from phishing attacks.
From a business perspective, lacking an SSL certificate can be a double-edged sword. Not only will search engines penalize your site by deprioritizing it in search results, but customers are also less likely to trust a website marked as “Not Secure.” For ecommerce, where user trust is everything, this can directly impact sales and brand perception.
For example, our luxury retail client renews their SSL certificate annually to maintain compliance and uphold the trust of their customers. This routine renewal ensures that the website remains secure, up-to-date, and fully compliant with evolving security standards.
Use web application firewalls
A web application firewall (WAF) is a critical line to secure an ecommerce website, much like an antivirus for your web applications. Its role is to filter and inspect incoming traffic to ensure only legitimate requests make it to your server and block malicious traffic before it can do any harm.
The same as an antivirus, a WAF has a database of known vulnerabilities and attack signatures. It allows the tool to detect and block the most common web application threats, particularly those in the OWASP Top 10, which includes SQL injections and XSS.
A WAF can mitigate even DDoS attacks, as it filters traffic and prevents your server from getting overwhelmed by requests. Though a WAF alone may not be enough to handle large-scale DDoS attacks, it’s an essential piece of the puzzle.
Not stopping there, WAFs can also be customized to enforce security policies, including managing cookie handling and session integrity, giving you an added layer of control over your website security.
When it comes to Java web application security, which is a common type of store in the ecommerce industry, WAFs protect against vulnerabilities often found in Java-based environments, such as RCE and unvalidated input.
Protect against data leakage
For ecommerce platforms, a single breach can cripple customer trust, invite regulatory penalties, and cause massive financial losses averaging $4.88 million in 2024, according to the IBM Cost of a Data Breach Report. Whether due to accidental exposure or targeted attacks, data breach prevention should be at the forefront of securing ecommerce website strategy.
Here, data loss prevention (DLP) software can help. DLP flags sensitive data such as credit card numbers, social security numbers, and personally identifiable information (PII) and monitors data flow within an organization, detecting and preventing breaches before they happen.
In addition to identifying risks, DLP tools:
- Provide data encryption strength to ensure that even if data is intercepted, it cannot be easily accessed.
- Deliver detailed reporting and analytics to help organizations stay compliant with data protection regulations and maintain data integrity.
Common DLP solutions include Microsoft 365 DLP, Symantec Endpoint Protection, and McAfee DLP, which offer robust protection for enterprise-level applications.
However, DLP is only part of the security features required for an ecommerce website. Data breach detection and prevention methods also include writing secure code and building a strong infrastructure that eliminates network vulnerabilities.
And since breaches can still happen, you should have a data breach response plan with steps for identifying, containing, and responding to breaches while ensuring compliance with legal requirements.
Regulate user accesses
While this security feature for ecommerce websites may seem not really about safety, it’s still an important security practice in ecommerce, in which various roles, from customer support to administrators, interact with the platform. Consider the impact if a compromised support account had full access to financial data or admin settings. The result could be catastrophic, leading to order fraud, payment fraud, etc.
To prevent this, OWASP (Open Web Application Security Project) recommends following the “principle of least privilege.” This means granting users only the permissions they need to perform their tasks, helping avoid two major risks:
-
Unintentional errors.
A user with more access than they need might unknowingly make changes or perform actions that can disrupt the system.
-
Exploitation by attackers.
If a user's account or device is compromised, attackers can exploit elevated permissions to steal sensitive data or sabotage your operations.
So, assign users predefined roles with specific permissions tailored to their responsibilities and conduct frequent audits to ensure that no one has unnecessary or outdated access.
Remember, even with strict access controls, issues can be in place, so data breach detection methods are crucial for monitoring unauthorized access attempts and ensuring that no one can exploit elevated permissions.
Prevent account hijacking
As many companies already know how to secure ecommerce websites from SQL injections and XSS attacks, — says OWASP’s top vulnerabilities report, — new issues have come into focus, such as preventing account hijacking.
Among fraud prevention features that safeguard against account hijacking, we can name:
-
Login location and IP tracking
If an account is accessed from an unfamiliar device or location, the scanning method helps users act before a breach occurs.
-
Password storage methods
Hashing passwords ensures that even if attackers gain access to your database, they can’t easily retrieve user credentials.
Additionally, a consistent scanning frequency can help detect suspicious login attempts and potential account hijacking activities, allowing for quicker response times.
Use multi-factor authentication
With 86% of breaches involving stolen credentials, according to Google Cloud’s 2023 Threat Horizons Report, password management and protection alone isn’t always enough. Multi-factor authentication (MFA) is a best practice here.
However, its application in ecommerce comes with a set of challenges, as it’s not always a user-friendly option. Customers prefer simplicity when shopping, often resisting complex password strength requirements, let alone additional authentication steps.
For many businesses, it comes down to balancing security with user convenience and determining how much risk they’re willing to accept to make the shopping experience seamless.
While MFA may not always be suitable for end-users, it’s highly recommended for securing back-office systems. Protecting admin panels and sensitive back-end functions with MFA along with password management adds another layer of security, ensuring that even if credentials are stolen, attackers won’t easily gain access.
Update regularly
Keeping your system up to date is one of the simplest still effective security measures for ecommerce websites that prevent online fraud. Regular updates address known vulnerabilities, making your platform far more resilient to attacks, as cybercriminals often target outdated software where weaknesses remain unpatched.
If you think that it’s okay to postpone updates a bit since there’s nothing very crucial about the latest update, don’t forget about zero-day vulnerabilities. It’s a security flaw that exists from the earliest version of an application but goes undetected until later.
Once identified and patched, all previous versions remain vulnerable unless they are updated. For example, a zero-day vulnerability in the WPgateway plugin led to attacks on 280,000 WordPress sites.
Except for your core systems, make sure to regularly update third-party libraries and employ vulnerability scanning methods to identify and fix issues early on.
Configure cookies properly
In the world of ecommerce cybersecurity, even something as small as a cookie can play a huge role in protecting your platform. Properly configuring cookies, especially those that manage user sessions, is a fraud prevention feature crucial for the security of ecommerce sites. Misconfigured cookies can be easily stolen, allowing attackers to hijack user sessions and compromise sensitive data.
To be more specific, properly configured cookies can reduce the risk of XSS attacks, as it’ll be difficult for attackers to exploit user sessions. At certain of our projects, we employ Akamai to manage cookie configuration, ensuring that every session is secure.
Use reliable payment providers
When it comes to payment fraud, the choice of your payment gateway is one of the most critical ecommerce website security requirements. It’s not just about the payment methods supported, it’s about ensuring that every transaction between your site and the payment provider is transmitted over a secure, encrypted protocol.
Make sure that your payment provider complies with the highest level of PCI DSS. While many ecommerce sites, including Expert Soft’s clients, also undergo PCI DSS certification, they aren’t required to meet the same stringent levels since they don’t store sensitive payment information like credit card or passport data. Payment providers, in turn, must adhere to the strictest standards because they handle and store all customer payment data.
But compliance alone isn’t enough. Even companies with numerous vulnerabilities can sometimes achieve certification. That’s why it’s equally important to choose a payment provider with a strong track record, solid reputation, and years of experience in the industry.
How to Increase Customer Trust in Your Site
Implementing strong security practices is essential, but it’s equally important to communicate these measures clearly to your customers. Use trust signals on your site to inform users that their data is in safe hands. Below are some key certifications and regulations that serve as trust signals to increase user confidence.
-
PCI DSS (Payment Card Industry Data Security Standard)
Already mentioned earlier in the article, this certification ensures that your ecommerce website meets security requirements for handling credit card transactions, reducing the risk of payment fraud, and protecting customer information.
-
GDPR (General Data Protection Regulation)
GDPR is the EU's regulation that governs how businesses handle personal data. For ecommerce sites, it requires transparency about data collection and usage while giving customers control over their personal information.
-
ISO/IEC 27001 (Information Security Management)
The certification sets the standard for managing sensitive information, helping ecommerce businesses establish and maintain a secure information management system.
-
SOC 2 (Service Organization Control 2)
SOC 2 compliance focuses on five key trust principles: security, availability, processing integrity, confidentiality, and privacy. For ecommerce, this certification is a clear trust signal that your platform maintains the highest standards of data protection and operational integrity.
Wrap up
In ecommerce, security is not just a technical requirement, it’s the foundation of customer trust and business continuity. Safeguarding payment data, protecting user accounts, addressing vulnerabilities, and implementing proactive security measures are critical to staying ahead of ever-evolving cyber threats.
By understanding the potential risks and leveraging the right security practices, ecommerce websites can not only defend against attacks but also build stronger, more trustworthy relationships with their customers.

Andreas Kozachenko is one of the founders of Expert Soft, a boutique ecommerce software delivery company. He has over 15 years of experience in the strategic leadership of ecommerce website solutions, ensuring their security and resiliency.
New articles

See more

See more

See more

See more

See more
